Product Overview
Cyber Security is about clarity
Understand your organization and where it stands in terms of Cyber Security.
Use our Risk Action Plan to mitigate risks.
Track your progress over time in your Cyber Security journey.
Compare business units to each other whether they be subsidiaries, departments, locations or whatever you choose.
Improve your Cyber-Vision
CIS - Centre for Internet Security
Choose the level of CIS you wish to implement:

NIST – National Institute of Standards and Technology (USA)
Whether you use the NIST framework or CIS, we enable you to view your cyber security using the NIST functions of Identify, Protect, Detect, Respond, Recover.

Assessments
- Set up how often you wish to do reviews - monthly, quarterly, bi-annually or annually.
- Define your team with relevant permissions for access.
- Using our assessment templates, simply determine the templates and sub-sets of templates you want to use (CIS 8.0 / NIST).
- Then set up your units - these could be subsidiary companies, departments, locations, separate businesses for consultants. Any way you wish to divide organizations.
- Once these actions are completed you can start your 1st assessments.

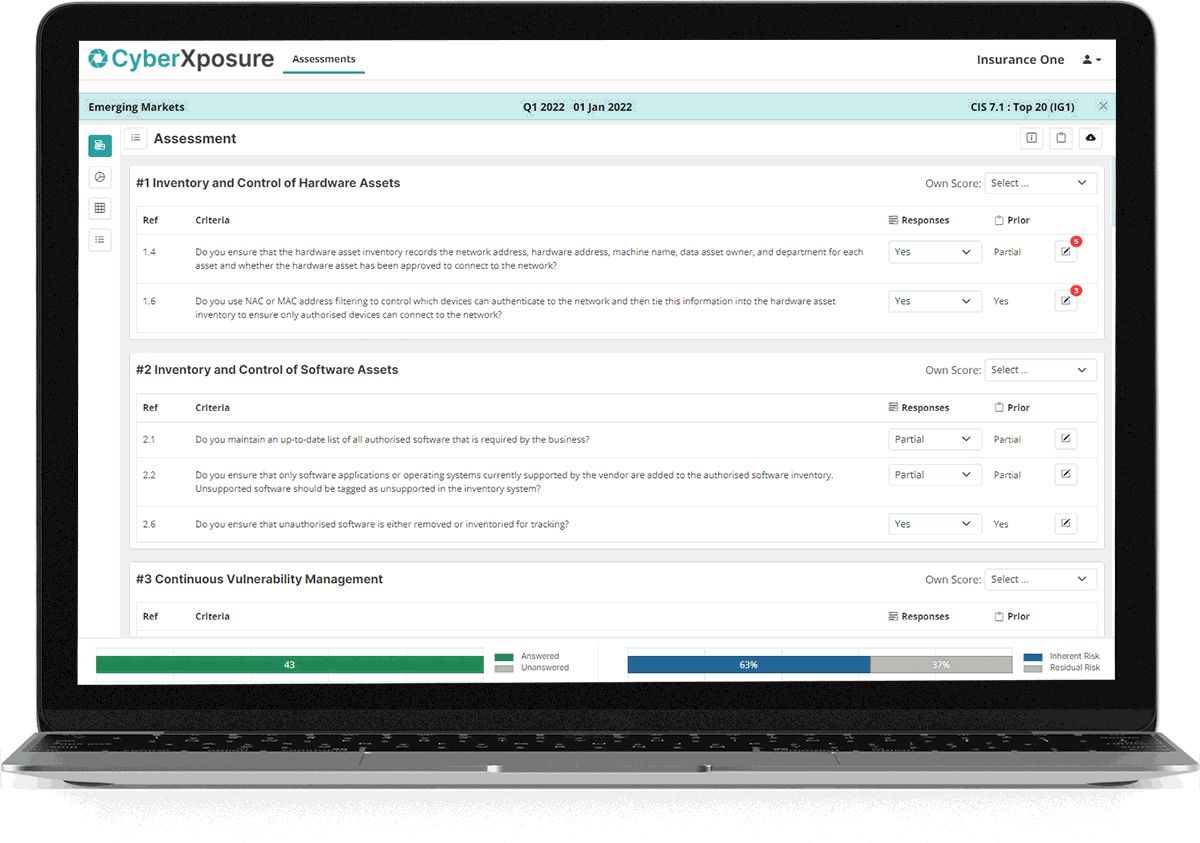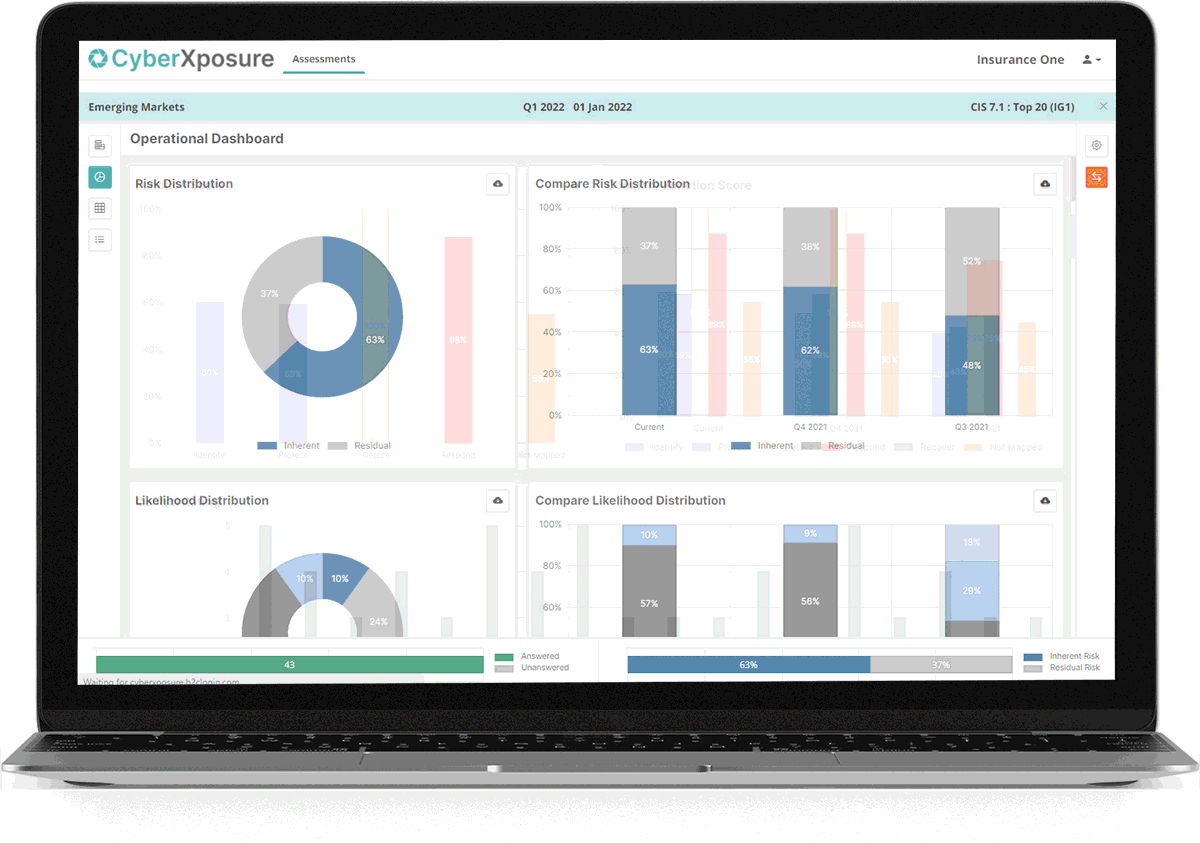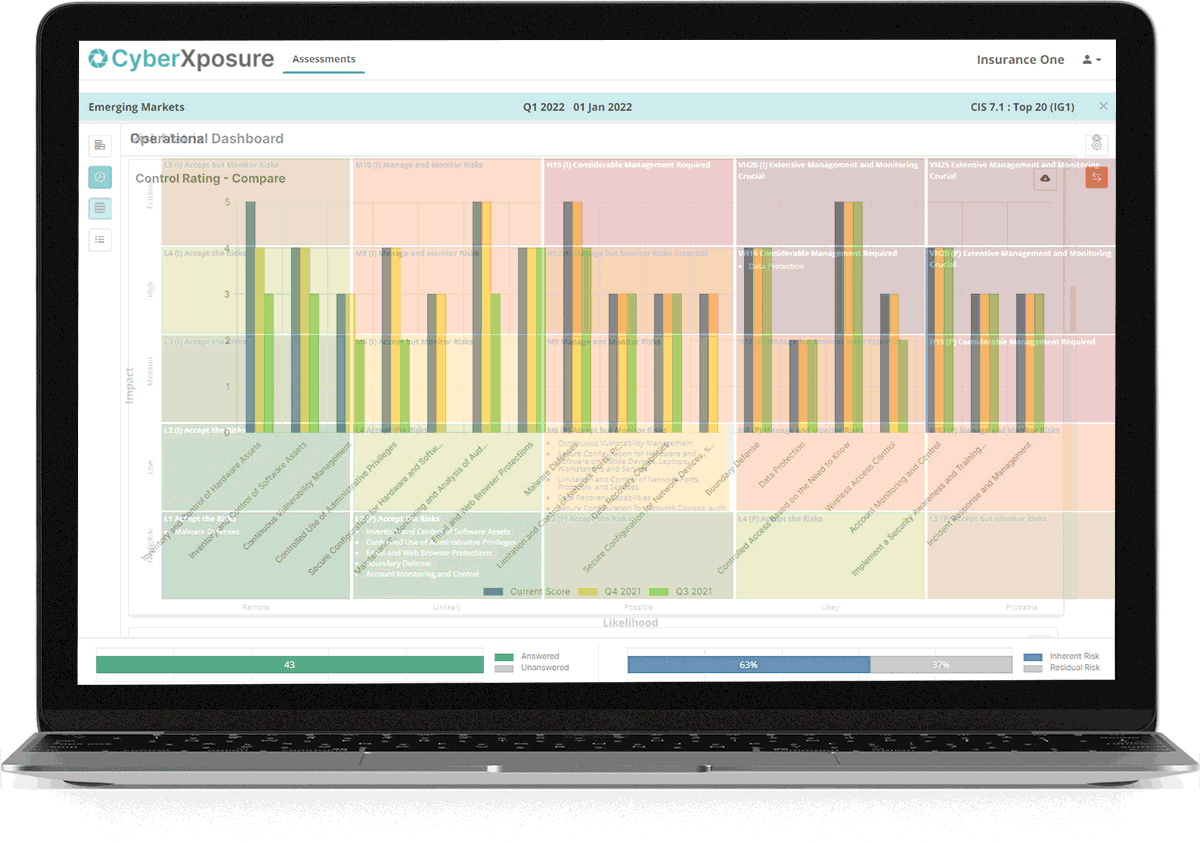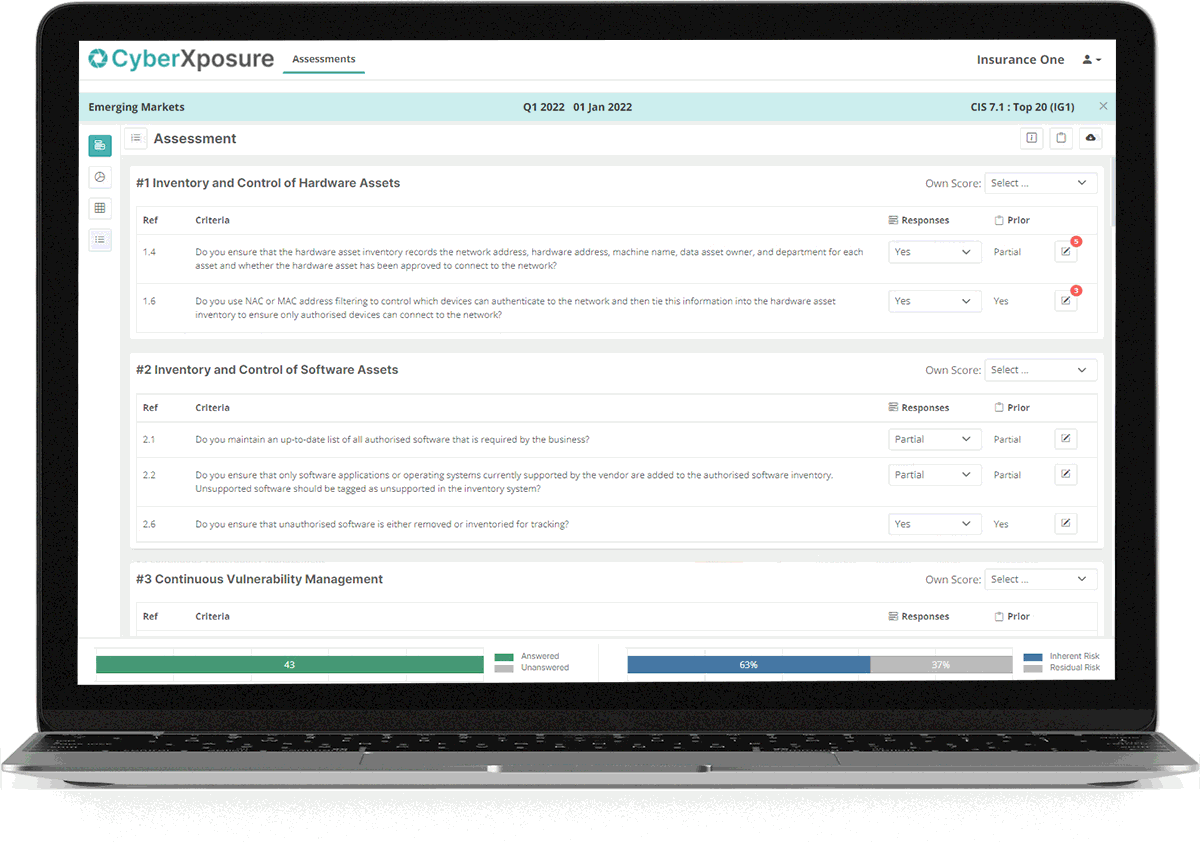
Assessment Capture
- Review each framework control and criteria.
- Set your expected score for the control then score each criteria.
- Add notes and files, “Evidence of Activity”.
- View results in graphs and the Risk Action Plan at any point.
- Take action based on recommendations in the Risk Action Plan.

Management Dashboard
The ability to look at your cyber-resilience status as an entire organisation is critical for management. Depending on how you have split your organisation - subsidiaries, departments, locations, equipment types, at some point you want to look at the entire organisation and compare across these.
Our management dashboard graphically provides:
- Inherent vs Residual Risk any Unit.
- Event likelihood by Unit.
- NIST Function score by Unit (Both for NIST and CIS based frameworks).
- Residual Risk by Unit across time.
- These are key to being able to report on progress (or lack thereof) to the organisation's leaders as required.

Risk Matrix
Our risk matrix looks at two axes, Impact and Likelihood. The grid of 25 blocks enables a very quick view of the controls / functions and where they fall in the matrix based on likelihood and impact. This analysis shows in one glance the areas of concern, colour coded to warn of danger. All reports, graphs and images can be exported for inclusion in external reports.
Assessment Dashboard
- View an individual assessment for a unit of the business, compare to pervious assessments for that unit.
- Look at Risk distribution, Likelihood Distribution, Function Scores (CIS and NIST), Control Ratings and comparisons, detailed assessment results.
- Add notes and files as “Evidence of activity”, build a full repository of Cyber Security information for each business unit.

Risk Action Plan
- When an assessment is in progress, we dynamically create a Risk Action Plan. This tells you exactly what actions need to be performed, all graded by KPI's, in order to move from a non-conforming to conforming position.
- When an assessment is completed, it may be that not all risk areas have been resolved. These remain available to view as a risk register and are actionable at any point, when the next review period comes up the issues can be set as completed.
- The Risk Action Plan is a key differentiator of our service, enabling automatic creation of tasks to perform in order to build cyber-resilience.

3rd Party Risk Management
- Create periodic assessments for 3rd parties.
- These can be using any framework in the system.
- Send directly to 3rd party.
- 3rd Party can complete the assessment and add unlimited evidence of activity per criteria.
- 3rd Party marks as completed.
- Assessment is reviewed, marked as Adequate OR Requiring remediation.
- Full report of each 3rd Party assessment is available.
- Each assessment can be compared with other 3rd Party Assessments.

Review, generate action plan, budget, rectify, monitor, review
Easily manage ongoing reviews of Cyber Security in your organisation.
Use the Risk Action Plan to rectify all issues arising.
Monitor your Cyber Security status on an ongoing basis.
Compare business units and their security stance to improve throughout your organization.