Doing a CIS IG1 Non-technical cyber assessment.
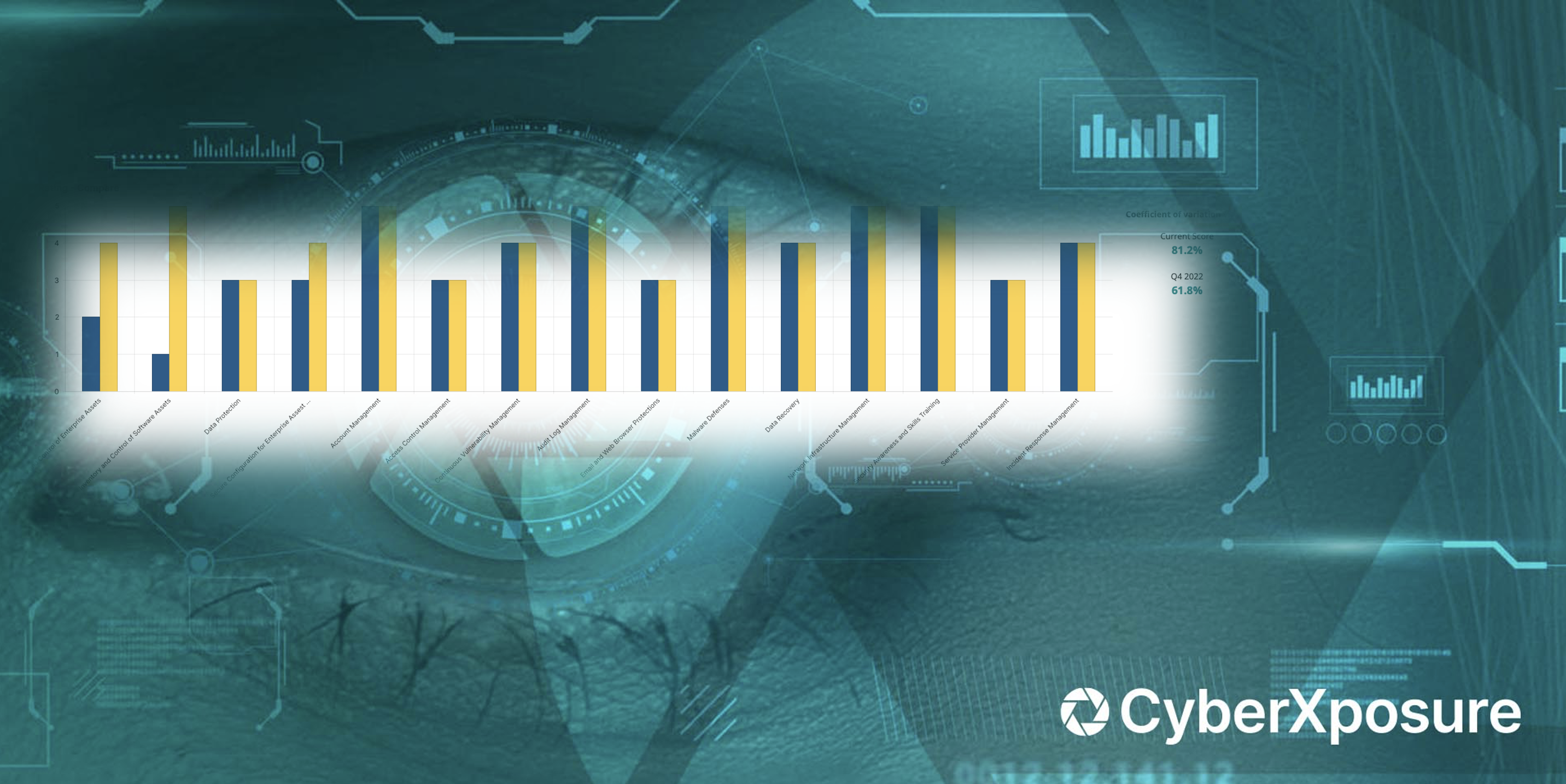
Performing a CIS IG1 cyber security assessment...
CIS IG1 controls 1 to 8 are a set of foundational cybersecurity controls developed by the Center for Internet Security (CIS). These controls are often referred to as "Hygiene Controls" because they represent the basic best practices that organizations should implement to maintain a basic level of cyber hygiene and reduce their risk of cyber attacks.
The CIS IG1 controls 1 to 8 are as follows:
Inventory and Control of Hardware Assets: This control involves creating and maintaining an inventory of all hardware assets (e.g., computers, servers, mobile devices) and ensuring they are properly secured.
Inventory and Control of Software Assets: This control involves creating and maintaining an inventory of all software assets (e.g., operating systems, applications) and ensuring they are properly secured.
Continuous Vulnerability Management: This control involves regularly scanning for vulnerabilities in hardware and software assets, and applying patches and updates in a timely manner.
Controlled Use of Administrative Privileges: This control involves restricting administrative privileges to only authorized personnel and monitoring their use.
Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations and Servers: This control involves configuring hardware and software to be secure by default, and implementing policies to ensure that secure configurations are maintained.
Maintenance, Monitoring, and Analysis of Audit Logs: This control involves logging and monitoring security events, and analyzing audit logs to detect and respond to security incidents.
Email and Web Browser Protections: This control involves implementing security measures to protect against phishing and other malicious email and web-based attacks.
Malware Defenses: This control involves implementing anti-malware measures, such as antivirus software, to detect and remove malware from systems.
Overall, the CIS IG1 controls 1 to 8 are known as "Hygiene Controls" because they are essential for maintaining a basic level of cyber hygiene and protecting against common cyber attacks. By implementing these controls, organizations can reduce their risk of cyber incidents and improve their overall cybersecurity posture.

Performing a CIS IG1 cyber security assessment...
CIS IG1, CIS IG2, and CIS IG3 are three different levels of...
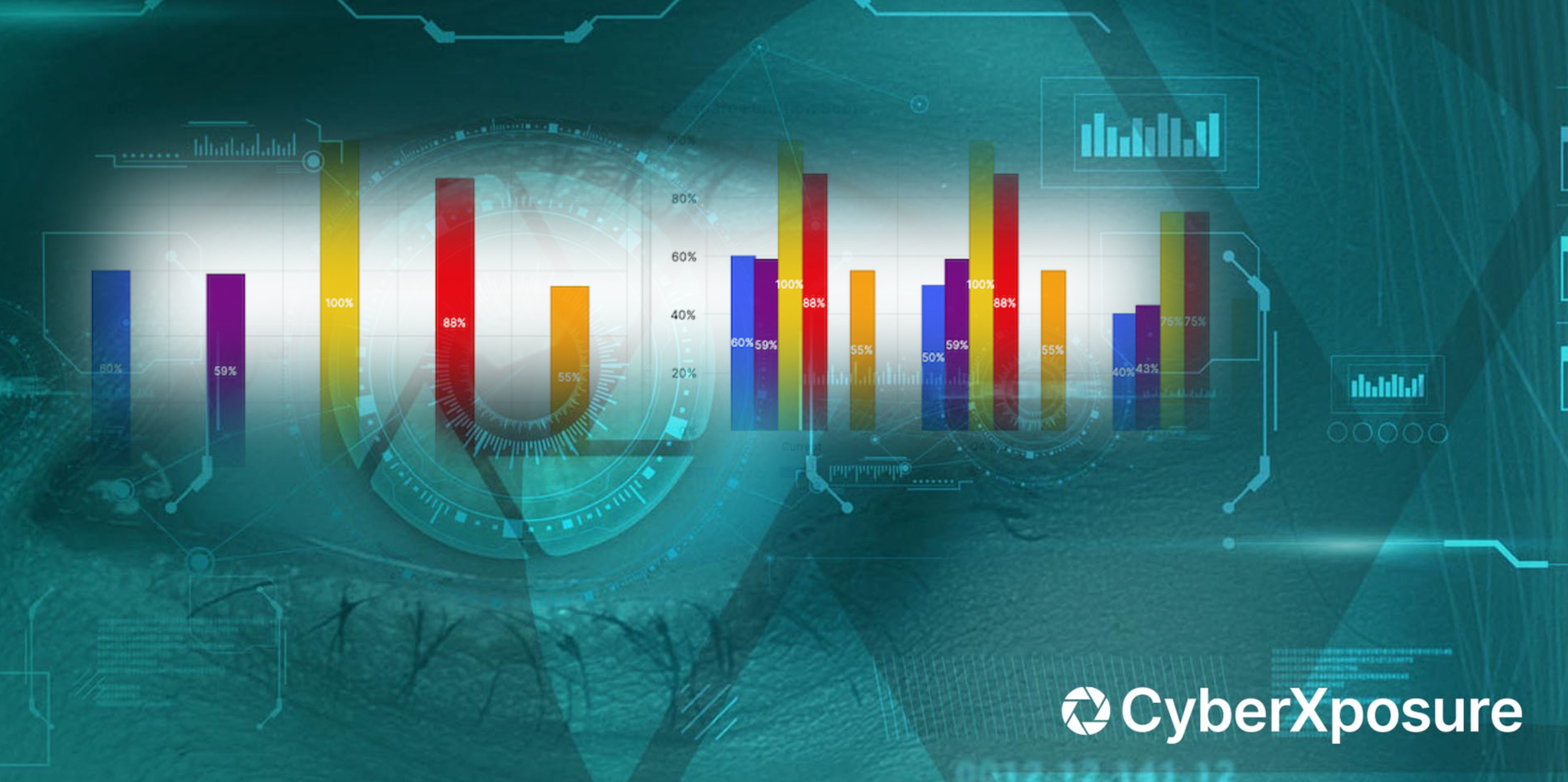
It is not a matter of one being better than the other; both the CIS Controls and the...
Blog comments